Penetration testing, a crucial component of modern cybersecurity, involves simulating cyberattacks to identify vulnerabilities in systems and applications. While its technical aspects are well-documented, the ethical considerations inherent in using such cyber tools are often under emphasized. This is where ethics and rules meet, making it essential to build an ethical way of thinking into every step of how penetration testing is done.
At its core, penetration testing operates in a grey area, deliberately searching for weaknesses that, if misused, could cause serious harm. At the same time, failing to maintain strong security through proper testing and timely patching of vulnerabilities leaves systems open to significant threats and breaches. Notable examples from 2024 include the Change Healthcare breach, where weak access controls and lack of multi-factor authentication allowed attackers to steal sensitive data. Similarly, Hertz suffered a major breach due to flaws in a third-party tool, compromising the data of over a million customers. In November 2024, Finastra discovered unauthorized access to its secure systems, highlighting weaknesses in internal security controls.
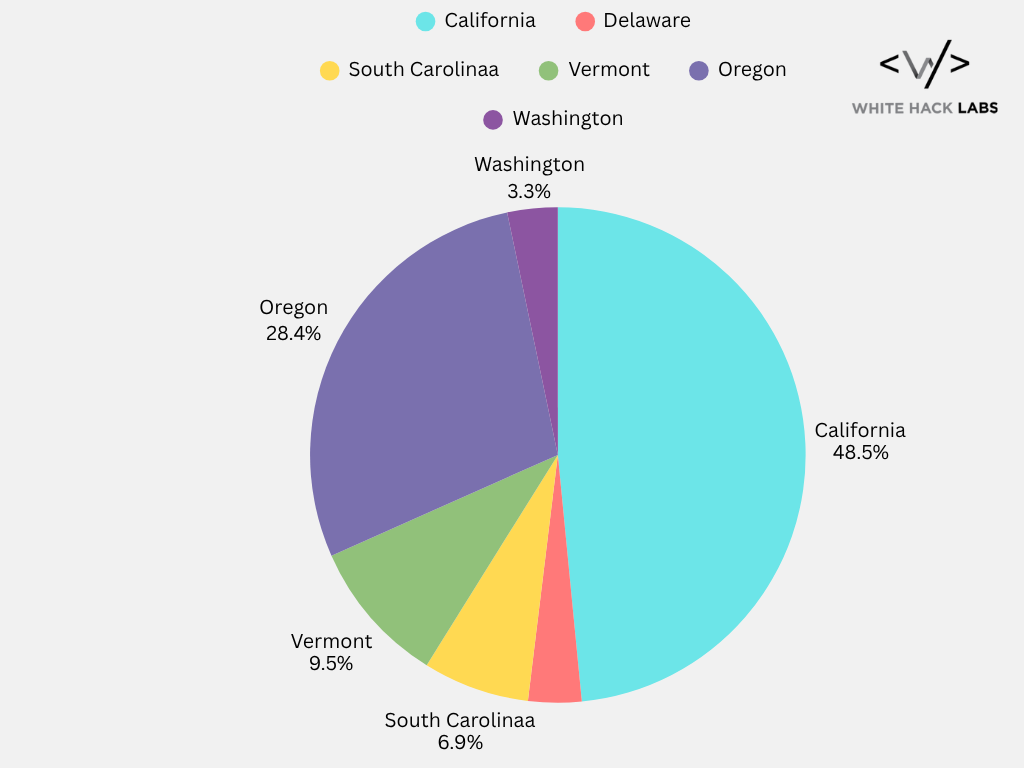
In 2025, data breaches reported by various U.S. state Attorneys General (AG) offices and other public sources highlight a continuing surge in cybersecurity incidents.
State | Department |
|---|---|
California | |
Delaware | |
Hawaii | |
Idaho | |
Massachusetts | |
North Dakota | |
Oklahoma | |
South Carolina | |
Texas | |
Vermont | |
Iowa | |
Maine | |
Oregon | |
Washington | |
Federal |
As of early 2025, 42% of U.S. states have passed data privacy laws requiring breach notification. Below is a chart illustrating the number of data breach records reported by each state in 2025 (until June 23rd ):
While it is important to perform penetration testing to keep a strong security posture, without clear ethical guidelines, even a well-meaning test can cross the line and become like hacking without permission.
This article aims to provide insights on how each stage of the penetration testing lifecycle such as scoping, execution, reporting, and remediation, carefully integrates ethical principles to ensure responsible and effective security assessments.
Exploring Engineering Ethics in Penetration Testing
The Ethical Divide Between Hacking and Penetration Testing
Hacking a system involves using technical skills, creativity, and cleverness to find surprising ways to take it over. Penetration testing is similar, but it has important rules. You still need those same skills to find weaknesses, but you can't damage the system or harm anyone's privacy or reputation in the process. Testers constantly face choices about what's allowed and what's not, from setting up the test to the methods they use.
The challenge intensifies because, even though the importance of ethics is universally acknowledged in this field, there's no clear, universally accepted guide on how to be ethical.
For example, the Open Source Security Testing Methodology Manual (OSSTM) advises considering ethics, but it doesn't provide practical steps on how to do so. This lack of explicit guidance highlights the need for a deeper dive into the ethical frameworks that do exist and how they attempt to bridge this gap.
So, navigating the ethical landscape of penetration testing will involve choosing from several models and frameworks that can help guide responsible decision-making. One influential approach is the Pierce et al. Model (2006), which places professional integrity at its core. It emphasizes avoiding conflicts of interest, reporting findings accurately, and adhering to legal and ethical standards to protect both clients and the broader cybersecurity field. However, critics argue that this model can oversimplify complex grey areas where legality and ethics may diverge.
More practical guidance comes from professional codes of conduct provided by organizations like EC-Council, CREST, and ISC. These codes stress the importance of obtaining explicit authorization, maintaining confidentiality, avoiding harm to systems, acting with professionalism, and responsibly disclosing vulnerabilities. Different ethical ideas help guide decisions in cybersecurity. The Deontological ethics is about following rules closely, like sticking to the agreed testing guidelines. On the other hand Consequentialism, or utilitarianism, looks at the results of actions and might support taking bigger risks if it helps prevent bigger problems later. A risk-based approach helps testers spot possible problems, think about how serious they are, and reduce risks by planning carefully and being open with everyone involved.
What are the Six Pillars of Ethical Penetration Testing ?
1. Transparency and Informed Consent: Defining Scope and Accountability
Underlying Ethical principle: Respect for autonomy and consent.
Transparency and informed consent are fundamental ethical principles that emphasize respect for autonomy and clear agreement. Before starting any penetration test, it is essential to explicitly define the scope by identifying which systems are authorized, who will conduct the assessment, and the tools and objectives involved. Ensuring full transparency around these elements guarantees that no system is tested without explicit approval and that all stakeholders understand the boundaries and implications of the test. Ethical penetration testing cannot operate under ambiguity; it relies on clear communication and informed permission as its foundational pillars.
2. Minimizing Harm: Responsible Methodologies and Boundaries
Underlying Ethical principle: Do no harm.
Minimizing harm is a core ethical principle focused on preventing unintentional damage during testing. Responsible methodologies include limiting tests to non-production or controlled environments whenever possible, using authenticated sessions with least privilege access, and scheduling tests during safe maintenance windows. These measures act as ethical safeguards to maintain system stability, protect data integrity, and avoid disrupting users. The goal is to simulate real-world threats in a controlled and responsible way that prioritizes safety throughout the testing process.
3. Justice and Fairness: Prioritizing Risk with Equity
Underlying Ethical principle: Fairness in addressing risk.
Justice and fairness in ethical testing mean prioritizing risks with equity. This involves categorizing vulnerabilities such as critical, high, medium, or low based on factors like their impact on business operations, the likelihood of exploitation, and the sensitivity of the data involved. The focus is on protecting the most vulnerable assets and users first, ensuring efforts reduce genuine risk rather than simply chasing novelty.
4. Honesty and Accountability: Evidence-Based Reporting
Underlying Ethical principle: Truthfulness and integrity.
Honesty and accountability are the center of truthfulness and integrity. A penetration testing report should provide reproducible results such as the payloads, logs, and screenshots, along with detailed impact analysis and practical remediation guidance. This commitment to evidence-based reporting ensures findings are communicated clearly, accurately, and completely, without exaggerating or minimizing the threats identified.
.
5. Responsibility in Action: Remediation and Follow-Up
Underlying Ethical principle: Duty to prevent future harm.
Responsibility in action reflects the ethical duty to prevent future harm. Discovering a vulnerability is only the beginning; critical findings must be remediated rather than merely acknowledged. Fixes should be validated through retesting, and long-term controls such as regression testing and integration into the software development lifecycle should be implemented. This approach acknowledges that responsible disclosure is incomplete without follow-through, aiming not just for detection but for lasting improvement.
6. Rigor Builds Trust: The Value of Manual Testing
Underlying Ethical principle: Competence and due diligence.
Rigor builds trust through competence and due diligence. While automated tools are helpful, they cannot replace expert human scrutiny. Manual testing is essential because human testers can identify subtle, context-specific issues, apply ethical judgment in assessing risks, and avoid overreliance on superficial scan results. This commitment to human-led testing ensures thoroughness, contextual understanding, and ethical awareness in technical decision-making.
Conclusion: Embedding Ethics into Cyber Defense
The guidelines put forth by WhiteHack Labs are not just technical requirements, but they're a codified ethical framework. Every step, from scoping to validation, embodies respect for privacy, responsibility, and fairness.
In this way, ethical penetration testing becomes not just a tool for improving security posture, but also a model for principled engineering. It is a deliberate fusion of intent and action, ensuring that our defenses are built not just for performance, but for trust.
Sources:
https://whitehacklabs.com/blog/what-are-the-ethics-of-penetration-testing
Various AG’s websites
https://cybersecurity.bournemouth.ac.uk/wp-content/papercite-data/pdf/fami15.pdf