
Introduction
Crypto hacks of 2022 focused almost exclusively on DeFi protocol. Attacks didn't target the blockchain technology itself. Instead, they targeted cross-chain exchanges where crypto of one blockchain could be exchanged for crypto of another. The damages are astonishing: almost 3bn stolen in crypto in 2022
Cross-chain exchanges or crypto bridges function as way to exchange crypto in between different blockchains. Normally the credit is issued on the destination blockchain and funds are placed in the special address on the source blockchain. This is where the concept of wrapped crypto originates. Wrapped BTC is a token on Ethereum blockchain that holds the value of BTC and could be used to exchange for ERC-20 tokens.
Major Incidents of 2022
Name | Amount Stolen | Month | Weakness Exploited |
|---|---|---|---|
Ronin Network | $625MM | March | Lack of decentralization, Interconnected validators |
Wormhole Bridge | $325MM | February | Lack of input validation |
Nomad Bridge | $190MM | August | Deployment mistake |
Beanstalk Farms | $182MM | April | Protocol governance flaw |
Wintermute | $162MM | October | Weak wallet address generation algo |
Mango Markets | $100MM | October | Price manipulation via Flash Loans |
Ronin Network
Ronin's proof-of-authority system, centralized in just nine validator nodes, is the key to its ability to provide a higher volume of transactions at a much lower cost than the proof-of-work ethereum network. Ronin network only had 9 validators instead of the entirety of nodes on the blockchain. An attacker was able to compromise 4 Ronin validators and find a backdoor to an external validator, having the majority to approve 2 illegitimate transactions that resulted in a loss of over $625MM.
Wormhole Bridge
Attacker cleverly exploited the lack of validation on auxillary input field of a signature validation function to execute its own code that minted out-of-blockchain wETH coins to be later converted to real ETH blockchain currency. The root problem was in usage of deprecated 'load_current_index' function that would skip input validation, instead of using 'load_current_index_checked' function that included validation.
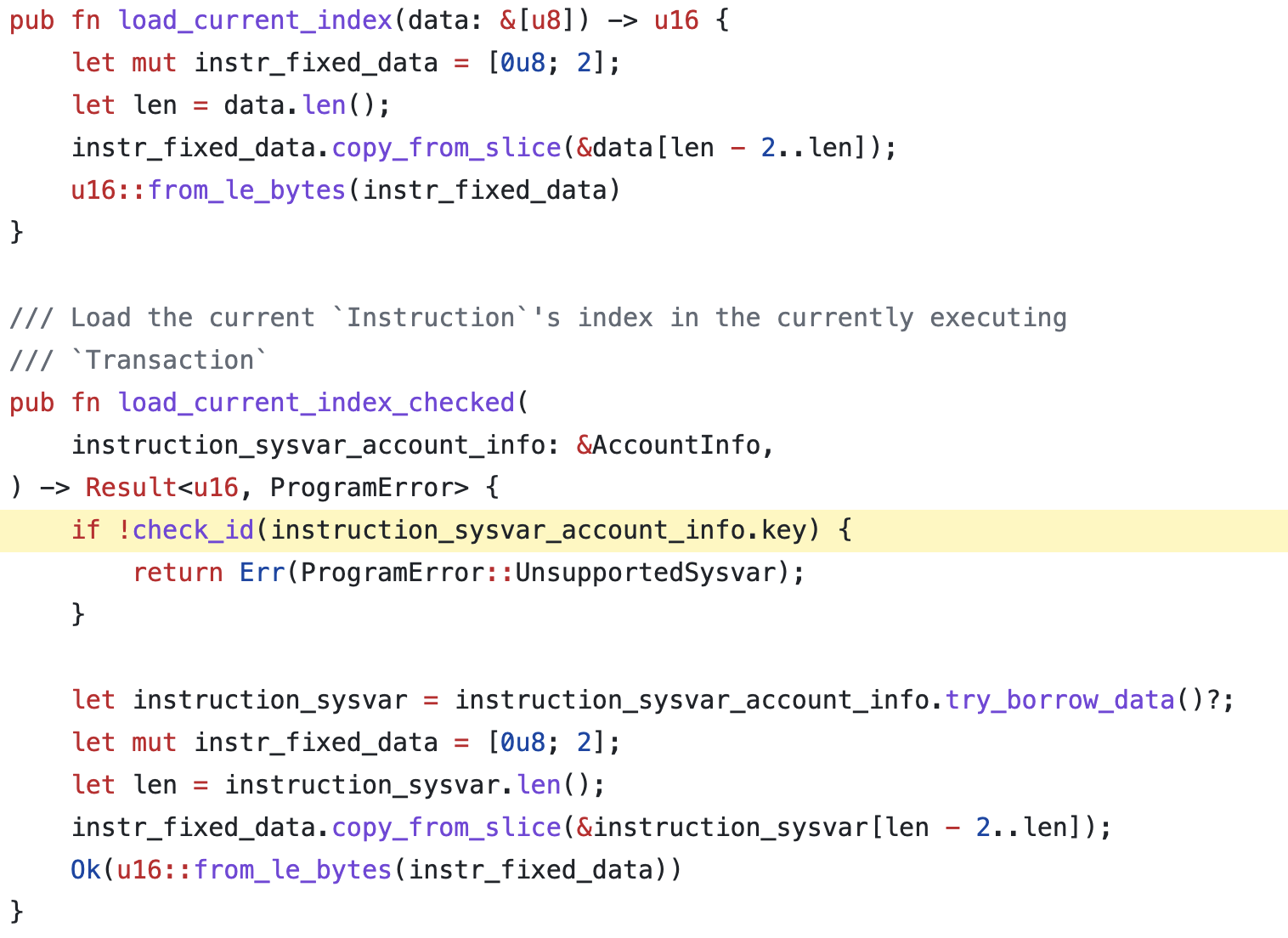
The intent to patch the issue became public in form of committed GitHub code right before the attack. It can be inferred that the attacker kept a close eye on a GitHub repository to look for any upcoming security patches before they got deployed.
Nomad Bridge
Nomad Bridge was hacked due to a mistake in the code that allowed anyone to take a valid transaction and change the recipient to attackers address. That would result in wrapped crypto being transferred in the attackers account. First attack transferred 100 BTC, others followed since everybody discovered vulnerability. The bridge was drained in a matter of days.
Replica contract was mistakedly initialized with `commitedRoot` value of zero. That allowed anyone to validate transactions by calling process(byte memory _message) function with an arbitrary "_message" to bypass the verification.
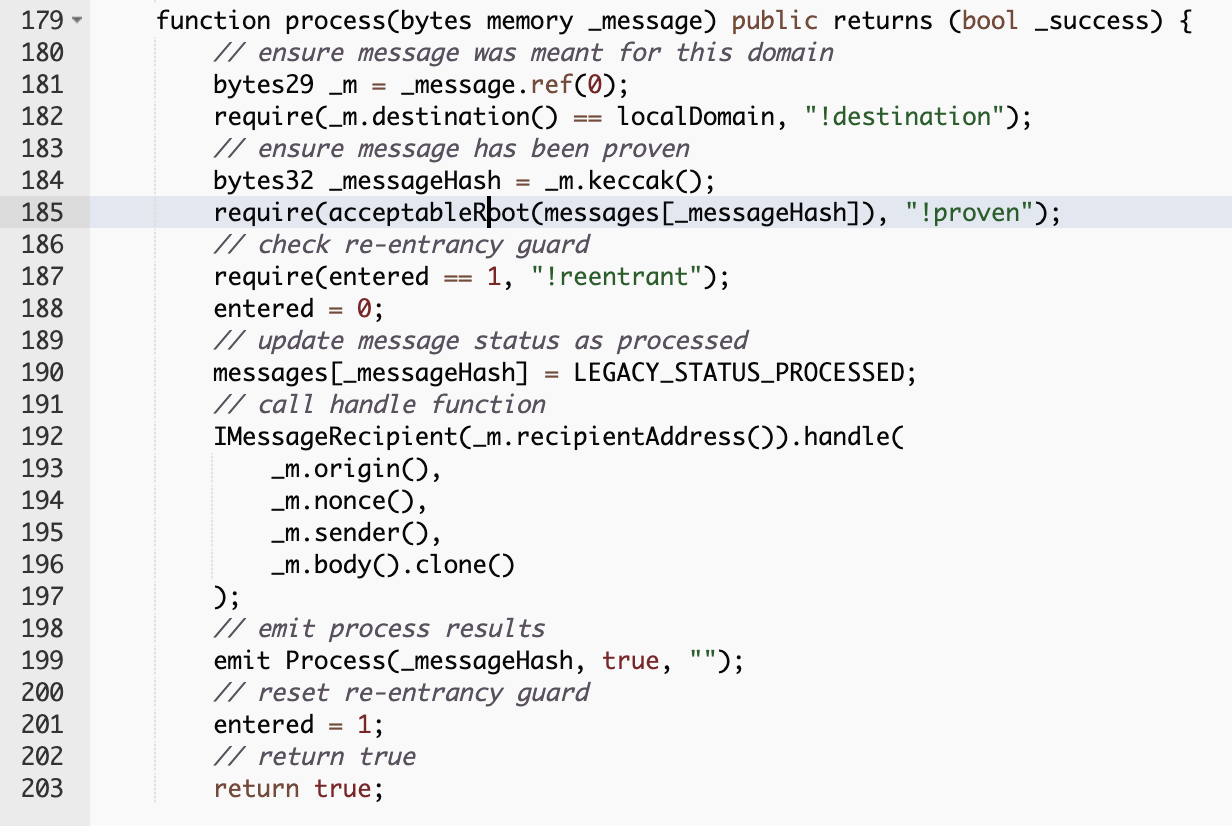
acceptableRoot function would always return true and let the function succeed instead of failing.
Beanstalk Farms
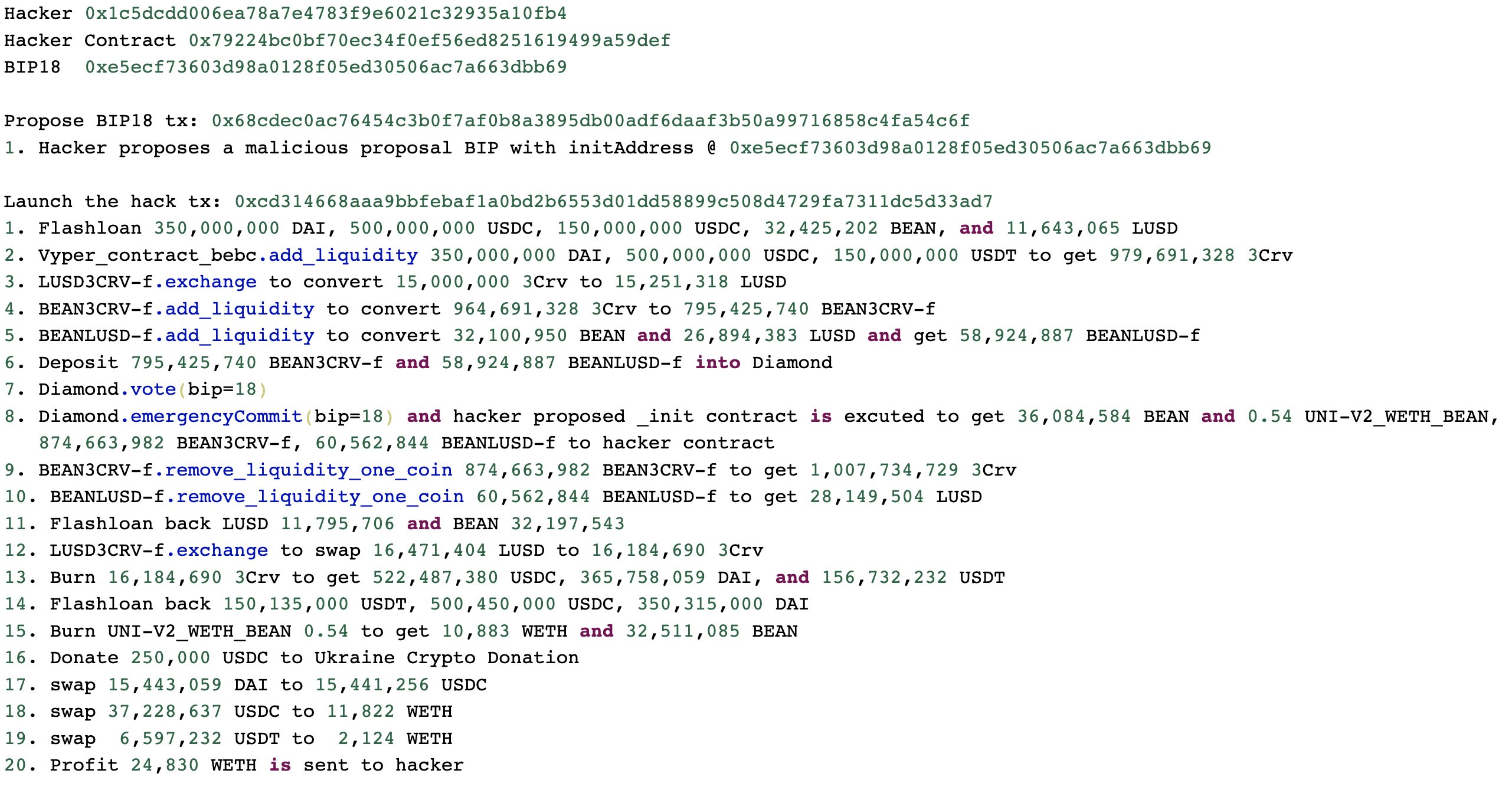
The attacker used a flash loan to accumulate a large amount of Beanstalk's native governance token STALK, which he then used to pass his own governance proposals (BIP-18 and BIP-19). These proposals asked the protocol to donate funds to Ukraine, but instead sent the funds to the attackers wallet.
Wintermute
Wintermute was a subject to an attack that resulted in 162.5MM in losses. The exploited weakness seem to have been the tool that generates Wallet addresses: Profinity. Due to security flaws of Profinity it was possible to decipher the private key from the wallet address. Attacker redirected funds using a brute-forced private key from Profinity generated wallet address.
Mango Markets
Solana DeFi Platform Mango Markets has been exploited by its primary function: Loans. DeFi platforms allow for taking out Flash Loans that have to be repaid before the end of block. That gives lenders about 10 minutes to repay them. DeFi is no stranger Price Oracle Manipulation with Flash Loans exploits, this is one of them.
The attacker made a substantial deposit of $5MM USDC and bought MNGO-PERP token. The prices of MNGO-PERP rose drastically in just few minutes which lead to collateral value of his account to go up. Attacker then took out massive loans and withdrew the funds.
We are currently investigating an incident where a hacker was able to drain funds from Mango via an oracle price manipulation. We will be disabling deposits on the front end as a precaution, and will keep you updated as the situation evolves.
The attack was made possible by a combination of lack of liquidity of token markets that are susceptible to manipulation and the fact that a volatile token can be considered a collateral for a loan.
Other typical crypto hacks
Reentrancy
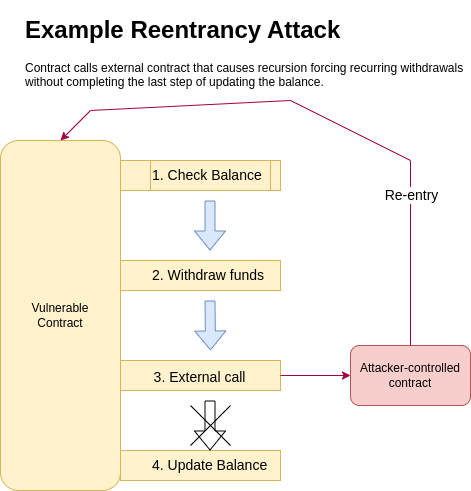
Reentrancy is when a procedure can be interrupted mid-way and "re-entered" or executed from the start in again, with the condition that both interrupted and re-entered execution complete successfully.
Business Logic Flaws
Most of the DeFI hacks are made possible by flaws in the business logic represented in code. It may be lack of input validation or ability to call any method of the DeFi platform by reference or ability to use the same token on both sides of the transaction, like it was demonstrated in 2021 MonoX Finance hack:
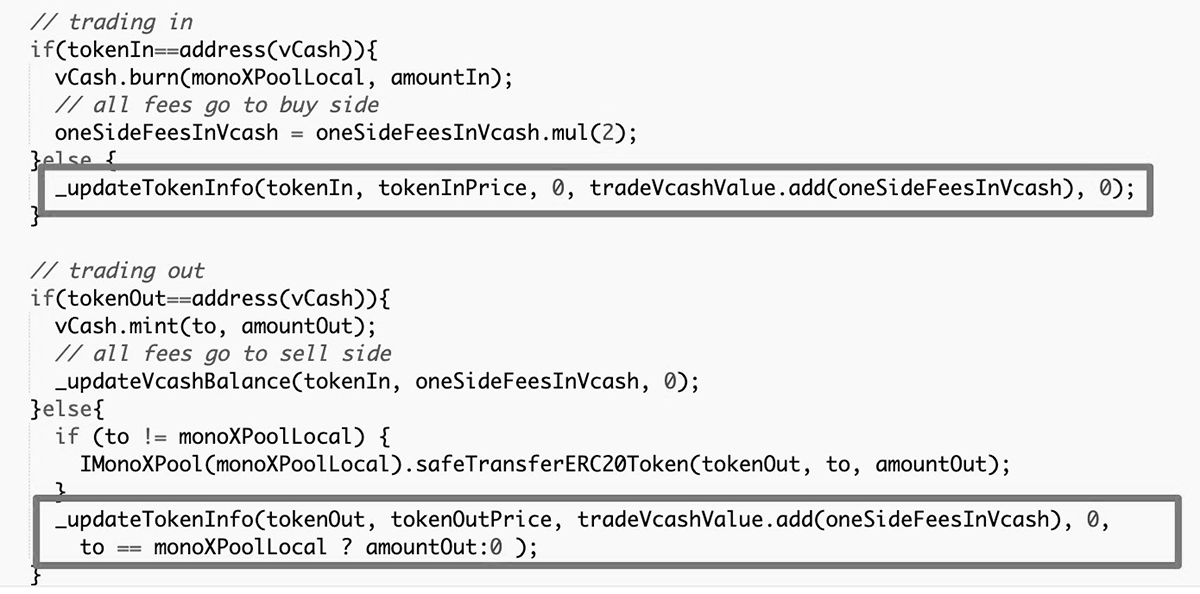
Conclusion
Crypto infrastructure is experiencing growing pains due to one of its virtues: Automation. Code is written by humans and when a human makes a mistake in code, it leads to exponential risk exposure of millions of lost funds. There are processes to prevent that, like SAST, DAST, SDLC. The bottom line, code updates require a review by other humans who will look at it from the perspective of an attacker.
Crypto holds real value, however many perceive it to still be somewhat of a game currency.

