
Introduction
It is essential to give network security top priority in the ever-expanding world we live in today, where our lives are intricately intertwined with the virtual world. We need to take enhanced precautions to preserve information since cyber dangers are growing. Penetration testing is useful in this situation, a component of cybersecurity that strengthens network security.
Understanding Penetration Testing
Pen testing, also referred to as penetration testing, simulates a cyberattack on a computer system, network, or application to determine how secure it is. Finding vulnerabilities that individuals could exploit rather than doing harm to them is the aim. Using this strategy, organizations can. Prior to crooks exploiting vulnerabilities, take action to address them.
The Four Stages of Penetration Testing
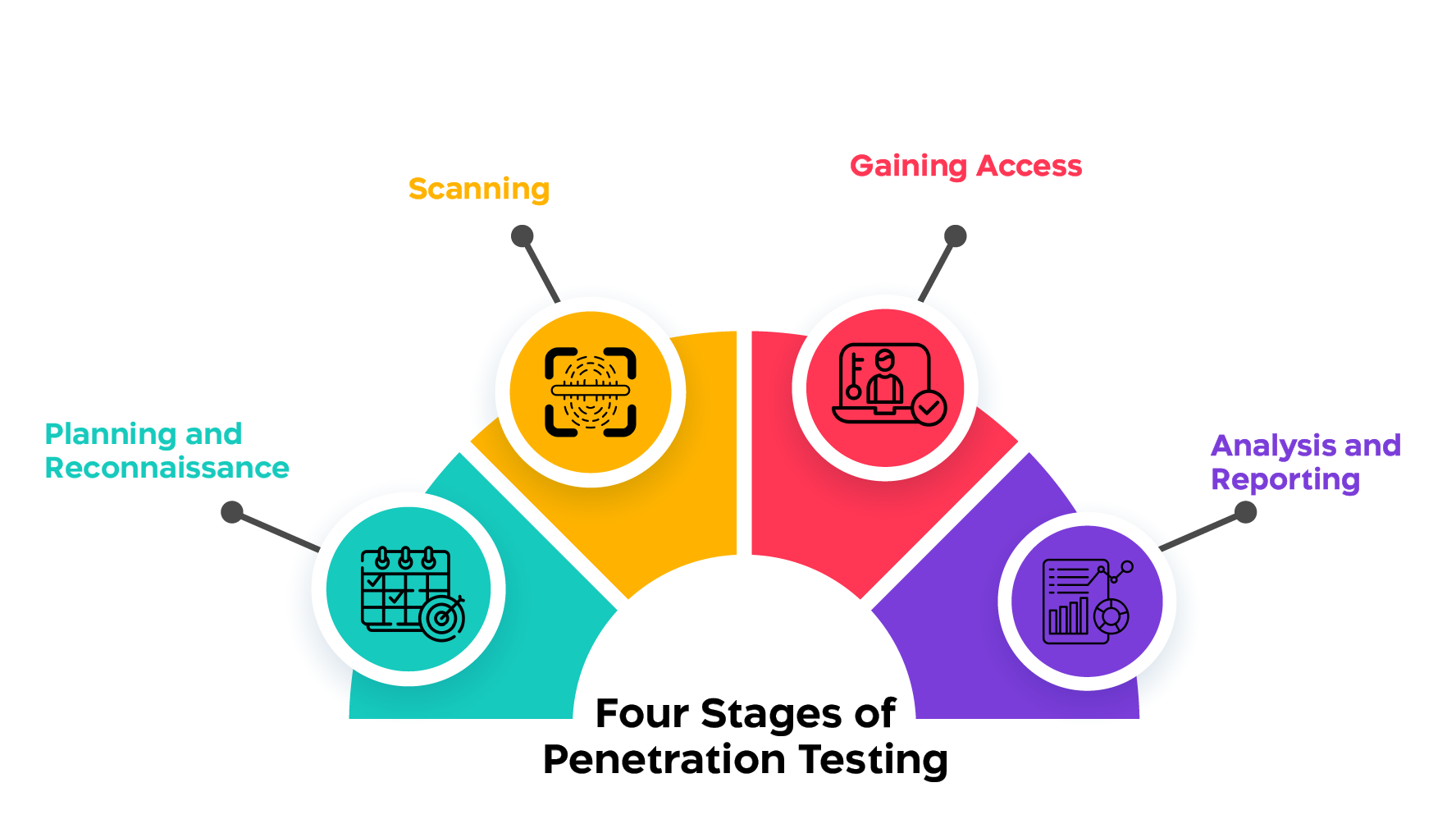
Planning and Reconnaissance: During this phase several important steps are taken. This includes defining the scope of the test, identifying target systems and gathering information about the environment being tested. At White Hack Labs we meticulously plan each engagement to ensure an understanding of our clients infrastructure and potential vulnerabilities.
Scanning: During this stage, To assess the client's network for vulnerabilities our skilled penetration testers utilize tools and cutting edge scanning techniques. At White Hack Labs no stone is left unturned as we conduct assessments of our clients networks.
Gaining Access: The penetration testers search for weaknesses in the target system and attempt to exploit them in order to get access during this phase of the simulated attack. White Hack Labs evaluates our clients' security posture by simulating real-world risks through hacking tactics.
Analysis and Reporting: The penetration testing team compiles a thorough report after analyzing the results of the mock attack. In addition to reports, White Hack Labs provides its clients with actionable insights, recommendations that are specifically tailored to them, and a plan for strengthening their security measures.
Elevating Network Security through Penetration Testing

Identification of Vulnerabilities The discovery of vulnerabilities in a network or system is the primary advantage of penetration testing. There is never a secure infrastructure since new threats always surface. With the help of its knowledgeable ethical hackers, White Hack Labs painstakingly identifies any flaws so that businesses are aware of them and may fix them before they become exploitable. White Hack Labs provides a detailed understanding of potential security gaps by conducting extensive scans and ethical exploitation. Organizations can efficiently prioritize and allocate resources by using this data to remedy important vulnerabilities that could otherwise act as entry points for cyber adversaries.
Realistic Simulation of Cyber Attacks In contrast to theoretical risk evaluations, penetration testing offers a practical, actual cyberattack simulation. The tactics, techniques, and procedures (TTPs) used by real malicious actors are mimicked by White Hack Labs. Organizations can assess their preparedness and reaction capacities against changing cyberthreats by using this practical approach. White Hack Labs guarantees that our clients are battle-tested against a range of potential cyber threats by simulating a variety of attack scenarios, including those involving advanced persistent threats (APTs). By using this proactive testing approach, organizations can improve their incident response and recovery plans by gaining the expertise and information necessary.
Protection of Sensitive Data One of the main issues in modern times is data protection. Whether one is dealing with customer information, business secrets and intellectual property; unauthorized access can lead to terrible outcomes. White Hack Labs penetration testing provides a formidable countermeasure to data breaches. By identifying vulnerabilities, organizations may fortify their defenses against illegal access and data exfiltration. By doing this, the company guarantees adherence to data protection regulations in addition to the protection of its reputation.
Strengthening Security Posture Due to use of penetration testing data, the organizations are able to enhance their entire security posture. White Hack Labs do more than simply identifying vulnerabilities; it offers strategic advice and valuable intelligence to enhance security defenses. It may also refer to changes in network configurations, security updates or enhanced access controls. We make our concepts fit any company’s infrastructure by partnering with them closely. This customized method makes certain that security improvements are inline with the particular operational needs and risk tolerance of the organization.
Regulatory Compliance Compliance is in the regulation, but it also refers to moral corporate behaviour under data security regulations that are tightening. The penetration testing from White Hack Labs enables companies to achieve and exceed regulatory standards. Due to the regulatory expertise of White Hack Labs, it is possible that its penetration testing can meet compliance standards both industry- and location –based. Not only does this help keep companies out of legal trouble but it shows that these businesses respect the safety and privacy of their customers.
Preventing Downtime and Financial Loss A major hack would not only cause big disruptions but also significant losses. One of the proactive solutions to avoid such disruptions is penetration testing. With prompt detection and correction of weaknesses, vulnerabilities can be prevented from becoming disastrous results for an organization through a cyberattack. White Hack Labs recognizes the financial impact of cyber disasters and thus has changed its penetration testing method to reduce potential risks that may cause losses. Using this innovative approach, organisations can flourish in the digital age without falling prey to financial pressure that accompanies cyber-attacks.
Why White Hack Labs?

Within penetration testing, the testing team's knowledge and ethical standards are equally as important as the methodology used. Particularly in the areas of penetration testing and ethical hacking, White Hack Labs is a shining example of excellence. Every interaction demonstrates their dedication to offering complete solutions rather than just services.
Expert Ethical Hackers The core of White Hack Labs is a team consisting of experienced and certificated ethical hackers. These people have a good knowledge of cyber threats, attack pathways and defense mechanisms. Their knowledge reveals gaps that may be missed by automated scanning tools, leading to a comprehensive and insightful investigation of an organization’s security state.
Cutting-Edge Tools and Techniques White Hack Labs does not use only traditional testing methods. We use the most up-to-date tools and strategies to anticipate new threats. By using advanced testing methodologies, they are able to mimic the broad spectrum of cyber threats and hence have their customers prepared for changing approaches adopted by malicious actors.
Collaborative Approach Different from a fitting-all, White Hack Labs adopt the collaborative perspective in their engagements. We collaborate with multiple organizations to understand their specific issues, business procedures and risk tolerance. This collaborative nature eliminates the possibility that recommendations are merely technically sound but irrespective of organizational objectives and goals.
Transparent Reporting Transparency is highly valued by White Hack Labs. In fact, the reports that we provide cover beyond technical details to give both contextual information and prioritized recommendations. This transparency not only helps organizations understand their securityscape but also nurtures a culture of perpetual improvement and shared responsibility
Continuous Support and Education The world of cybersecurity is constantly changing, and White Hack Labs understands that the support for education has to be continuous. Apart from conducting penetration tests, we also provide continuous support to help organizations implement security improvements. Moreover, we provide learning materials that give clients the necessary knowledge to deal with an increasingly dynamic cybersecurity environment.
Conclusion
In the battlefield of constant changes between cyber attackers and defendants, penetration testing is a potent weapon used in building virtual fortresses. With our ethical hacking expertise and quality focus, White Hack Labs take the highest point in advancing network security. By undertaking careful testing, coordination, and comprehensive cybersecurity practices we enable organizations to comprehend the uncertainties of the digital world with fortitude.

