Unrestricted file upload is a commonplace problem among web applications. While its exploitation methodology is widely known the remediation techniques are hard to find. In this article we provide recommendations on how to address CWE-434.
File Upload Basic Restrictions
Set a maximum name length and maximum file size for uploaded files: Implement restrictions on the length of the file name and the maximum allowed file size. This helps prevent abuse and ensures efficient storage.
Randomize uploaded file names: Generate random file names for uploaded files to avoid predictable naming patterns and enhance security.
Store uploaded files outside the web root folder: Save uploaded files in a directory that is not directly accessible via the web server to enforce access controls and prevent unauthorized access and execution of uploaded files.
File Type Verification & Restriction
Verify file type on the server-side: Implement backend framework verification to check the actual MIME Type of uploaded files. Web application needs to ensure that the file extension specified by the user matches the actual content of the file, preventing malicious uploads. Relying on Mime Type from Content-Type header is not sufficient since the header can be spoofed by the attacker. Some of the open-source packages for file type verification:
ahupp/python-magic: A python wrapper for libmagic (github.com)
aki77/activestorage-validator: ActiveStorage blob validator. (github.com)
Limit file types: Specify the allowed file types by only allowing certain file extensions. This will help restrict upload-and-execute behavior commonly supported by following file types:
PDF
DOCX
XLSX
Scanning Uploaded Files for Malicious Content
Consider implementing a virus scanning solution to scan uploaded files for malware or malicious content. Options include free open source solutions like ClamAV and YARA, or commercial end-user solutions like Amazon S3 with Sophos or OPSWAT.
Scalable file processing pipeline: Utilize a scalable file processing pipeline that incorporates virus scanning tools. An example below is using AWS S3 as the core storage for uploaded files and employing pre-signed URLs for authentication and authorization. This ensures that only authenticated users can upload and download files.
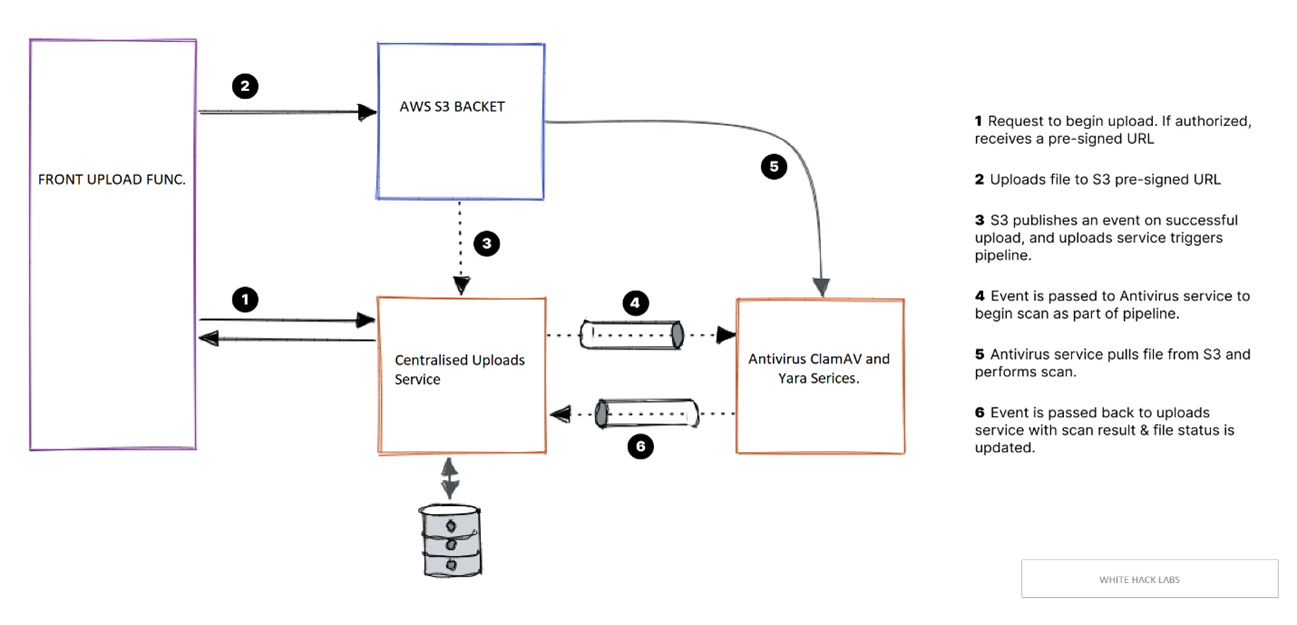
ClamAV and YARA integration: Integrate ClamAV and YARA rules into the file processing pipeline to scan uploaded files for viruses, malware, or any other predefined criteria. The scanning results should be published and used to update the file status in the uploads service, which determines whether the file can be accessed by other users.
Example YARA rule for PDF files
Below is the example YARA rule for scanning PDF files for executable JavaScript embedded in them:
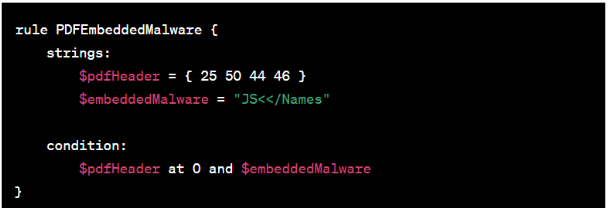
In this example, we're looking for the presence of the string "JS<</Names" within the PDF, which is a common indicator of malicious JavaScript code embedded within a PDF file. For more YARA rules, follow this link.
Conclusion
By implementing these file upload recommendations, you can enhance the security of your web application, protect against malware and malicious content, and ensure that only authorized users can access and interact with the uploaded files.

